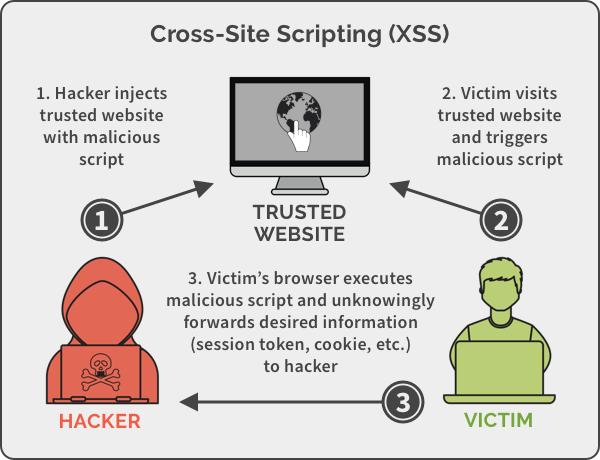
What is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a type of computer security vulnerability that enables attackers to inject malicious code into web applications. It is a form of malicious attack that exploits vulnerabilities in web applications to inject malicious scripts into web pages. XSS attacks are used by attackers to gain access to sensitive information, such as user accounts, passwords, or other confidential data.XSS attacks can occur when a web application accepts user input without validating it. This type of vulnerability allows an attacker to inject malicious code into a web page, which can then be executed by any user who visits the page. For example, an attacker could use XSS to inject malicious JavaScript code into a web page, which could then be executed by any user who visits the page. The malicious code could be used to steal user data or to perform other malicious activities.XSS attacks are one of the most common web application security vulnerabilities. They are particularly dangerous because they can be used to gain access to sensitive data and to perform malicious activities without the user’s knowledge. Therefore, it is important to understand the threat posed by XSS attacks and to take measures to protect against them.
Types of Cross-site scripting(XSS) attack
There are three primary types of XSS vulnerabilities:
- Reflected XSS: In reflected XSS attacks, malicious scripts are injected into URLs or form parameters and are reflected back to the user in the web application's response. When a user clicks on the malicious link or submits the form, the malicious script is executed in their browser
- Stored XSS: Stored XSS attacks occur when malicious scripts are permanently stored on the web server, typically within a database or a file system. These scripts are then executed whenever a user visits the affected page or resource.
- DOM-based XSS: DOM-based XSS attacks exploit vulnerabilities in the Document Object Model (DOM), which represents the structure of a web page. In this type of attack, malicious scripts manipulate the DOM directly, altering the content of a web page without requiring user interaction.
Exploiting XSS Vulnerabilities:
To truly understand the threat landscape, it is crucial to explore the methods employed by attackers to exploit XSS vulnerabilities. From classic attack vectors like input fields and form submissions to more sophisticated techniques utilizing AJAX requests and third-party integrations, hackers are continuously evolving their tactics. By examining real-world examples of successful XSS attacks, we can gain insights into the mindset of attackers and the potential consequences of a successful exploit.
Attackers employ various techniques to exploit XSS vulnerabilities and achieve their malicious goals. Some common exploitation methods include:
- Phishing attacks: Attackers can use XSS vulnerabilities to phish for sensitive information, such as login credentials or credit card details, by crafting malicious links or forms that mimic legitimate ones.
- Session hijacking: By injecting malicious scripts into web pages, attackers can steal user session cookies, allowing them to impersonate users and gain unauthorized access to their accounts.
- Malware distribution: XSS vulnerabilities can be exploited to distribute malware by redirecting users to malicious websites or by embedding malicious code directly into web pages.
Mitigating XSS Vulnerabilities
Effectively mitigating XSS vulnerabilities requires a comprehensive approach that encompasses both preventative measures and proactive monitoring. Here are some key strategies to consider:
- Input validation: Implement robust input validation mechanisms to ensure that user-supplied data is sanitized and free from potentially malicious code before being processed or displayed.
- Output encoding: Encode all user-generated output before it is rendered in the user's browser to prevent malicious scripts from being executed.
- Content Security Policy (CSP): Implement a CSP to define a whitelist of allowed sources for scripts and other content that can be executed on the web page.
- Web application firewalls (WAFs): Utilize WAFs to filter and block malicious traffic attempting to exploit XSS vulnerabilities.
- Regular security audits: Conduct regular security audits to identify and remediate XSS vulnerabilities proactively.
- Educate developers and users: Provide training and awareness programs to developers and users about XSS vulnerabilities and safe coding practices.
Conclusion
Cross-site scripting (XSS) is a type of vulnerability that allows attackers to inject malicious code into web applications, allowing them to access sensitive data, modify website content, and even take control of user accounts. XSS is a serious threat to web security and it is important to understand how XSS works, how to exploit XSS vulnerabilities, and how to mitigate XSS attacks.In conclusion, XSS is a serious threat to web security and it is important to understand how to identify, exploit, and mitigate XSS vulnerabilities. It is also important to remember that XSS attacks can be difficult to detect and prevent, so it is important to use secure coding practices and to keep all web applications up-to-date with the latest security patches. By following these best practices, organizations can reduce their risk of falling victim to XSS attacks.